Did you know? Companies lose 400,000 million dollars to hackers each year?
In 2021, the figure may hit 600 billion dollars because the next generation of computers would be affordable, faster, and better.
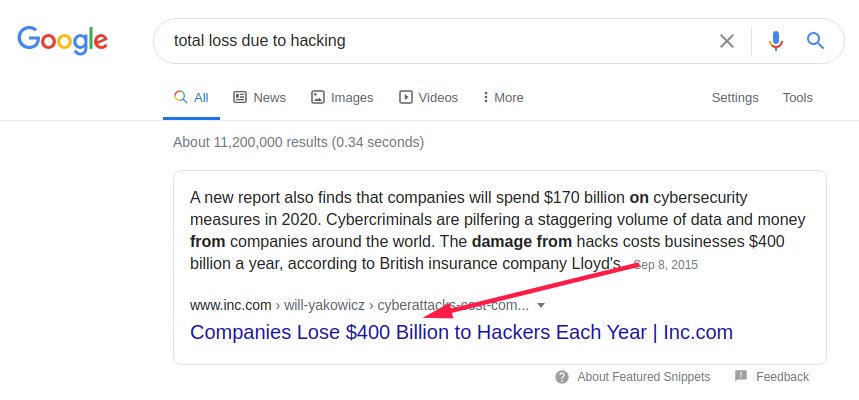
That’s a frightening figure, isn’t it?
Most mobile developers don’t care until a hacker compromises their apps. 😢
Isn’t it better to use the Firebase Storage Rules smartly? Of course.
The best part?
You don’t have to manage infrastructure or even write sophisticated server-side authentication and authorization code, and you can focus on a great UX.
Quick Jumps
Understand the Basics of Security in Firebase
Do you know?
In order to hack anything, you need to understand how that thing works. 😀
Moreover, Firebase Auth helps your user to authenticate into your app.
Also, Firebase storage security rules make it very simple for you to approve (authorize) the users and validate their requests.
[the_ad id=”3750″]
Just a few chunks of code are enough to prevent or access specific users to specific content.
Similarly, you must know the basic component of security embedded in almost any security app.
Here we go:
Authentication:
Authentication is a significant part of the creation of the application.
Firebase presents an easy way to use, a safe authentication system for user side authentication.
If you want to configure user-based security rules, then you must set your app with Firebase authentication.
When a client-side user is verified with Firebase Auth, the request.auth variable in Firebase cloud Storage Security Rules shifts to an object that includes the user’s UID (request.auth.uid) and all extra client user knowledge in the token (request.auth.token).
Whenever any of the users not authenticated into the app; it means request.auth the variable is null. It lets you manage data access on every user. Read more in the User Security portion.
You may be interested in reading:
- Facebook Login for Android Easy Tutorial [With Video]
- Firebase Anonymous Login Android (Easy Tutorial)
- Sign Up/Sign In With A Phone Number Using Firebase (Guide)
Authorization:
Authorization plays a vital role in terms of security since it allows you to know who your users are.
If you can check who your users are, then you can assign some rules to the user.
For instance, you can assign a small portion of users who are capable of writing the content or reading the picture, etc.
Moreover, default Security Rules of Cloud Storage need Authentication service of Firebase in order to perform any. write read or operations on all the files:
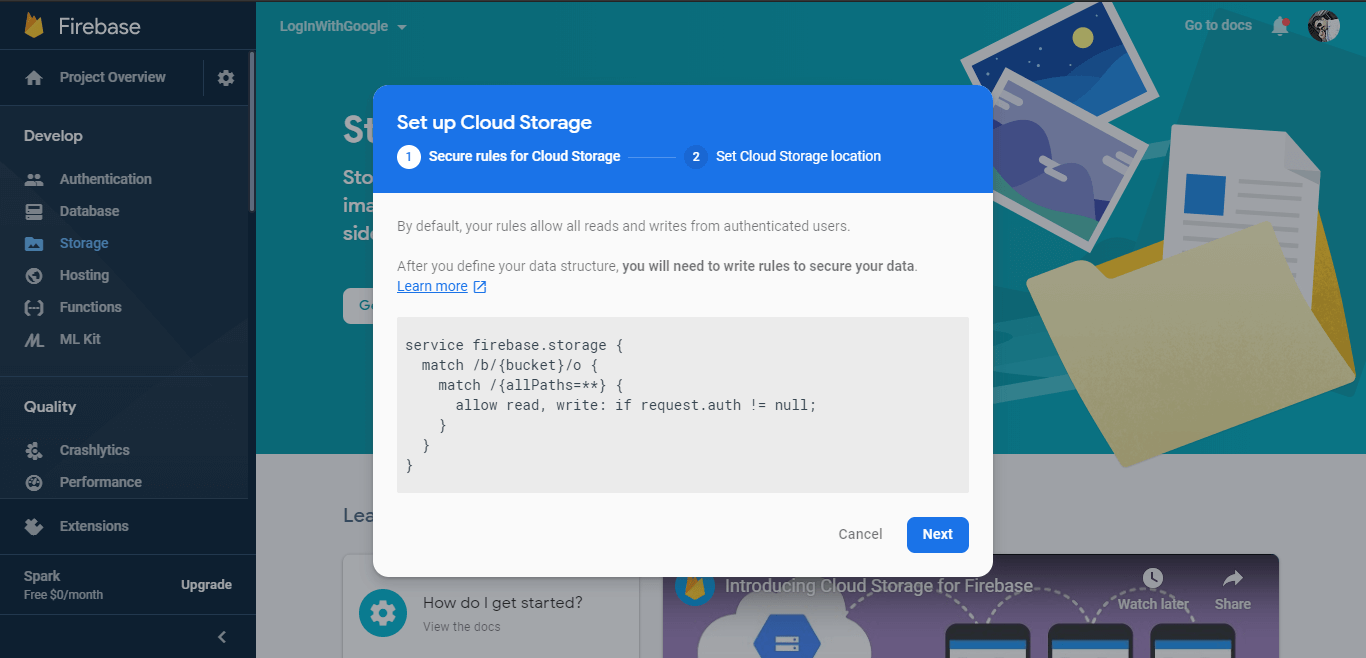
You can also change the rules in the Firebase Console in the rules tabs of Storage navigation.
Data Validation:
Security rules of Cloud Storage can also be handled in the data validation.
It means you can validate the path, name of the file, and file metadata properties like content-type and size, etc.
Now the basic portion of security rules is completed, let’s dive into the practical portion.
Create Storage Security Rules In Firebase console:
First of all, go to Firebase Console and select your existing project.
Don’t have a project? Kindly create a new one.
Now here you can see your default security rules, and click Next.
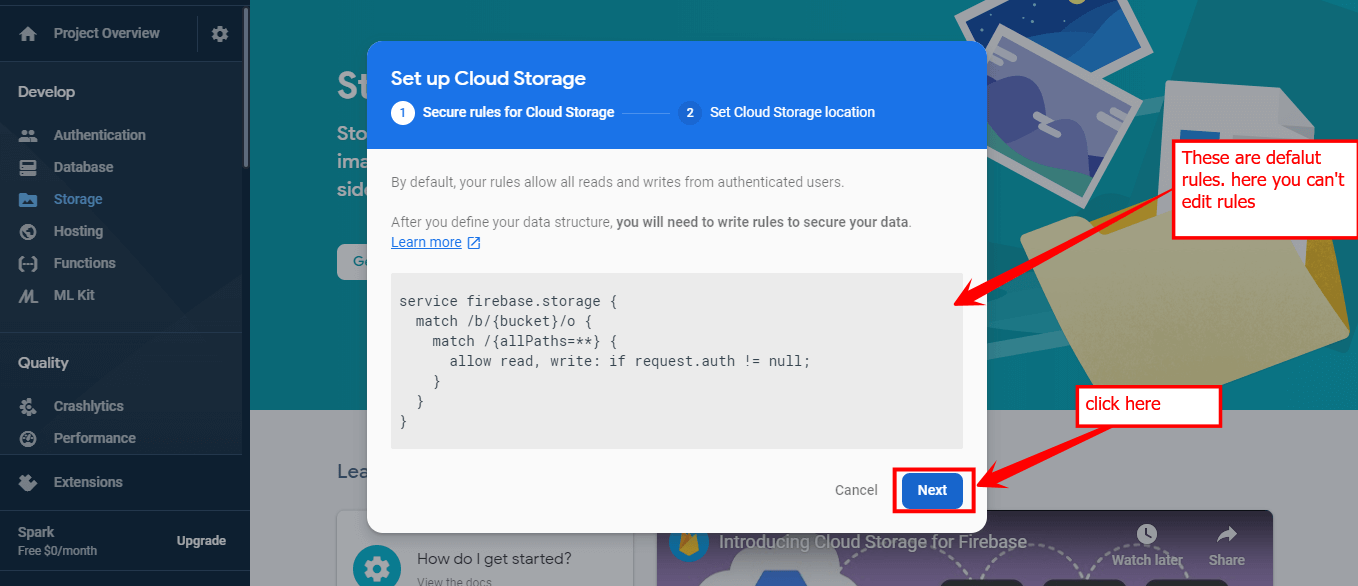
Afterward, select cloud storage server location and click done.
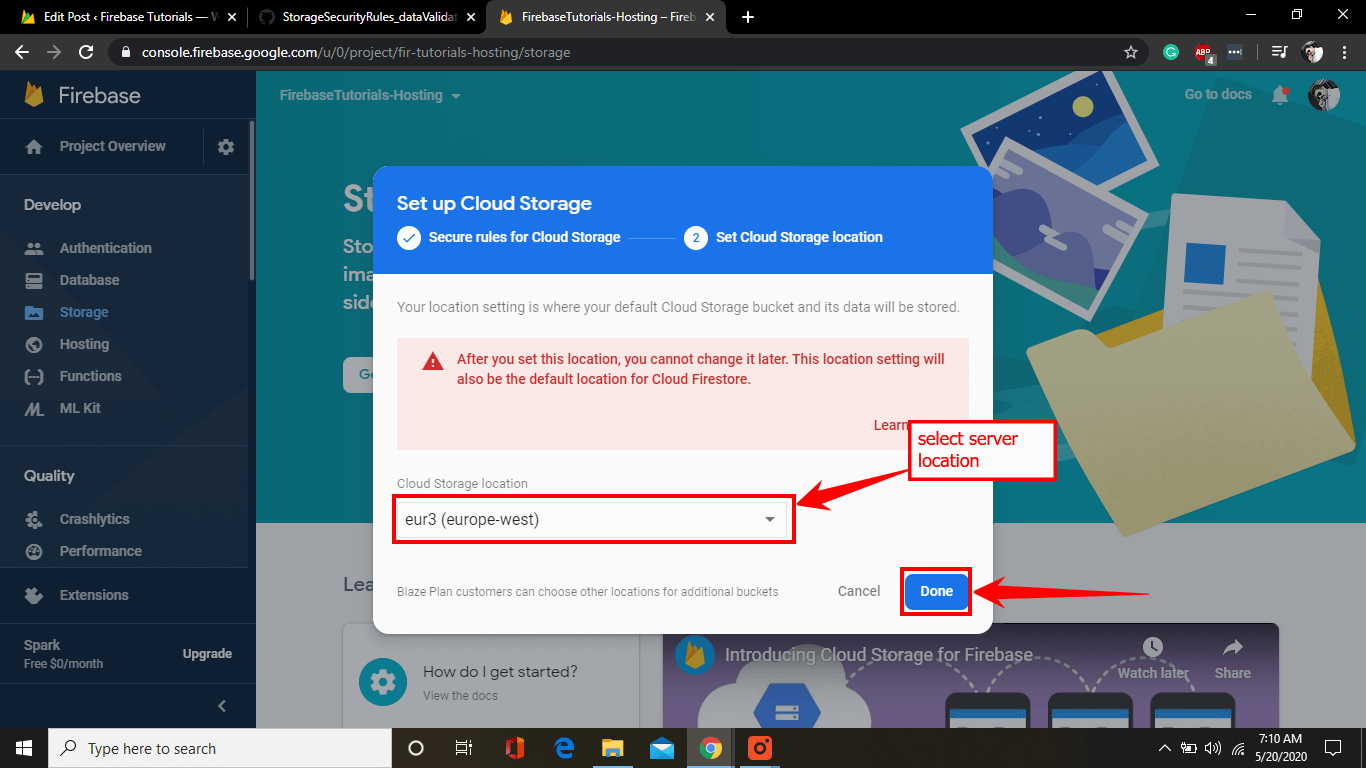
It’ll take a few seconds to load your project entirely.
Next, you can see your Dashboard just like in the below image:
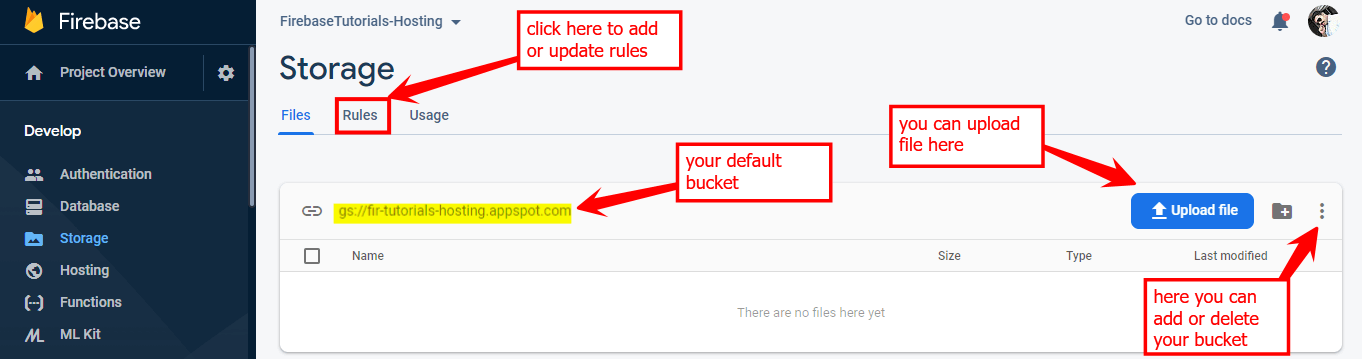
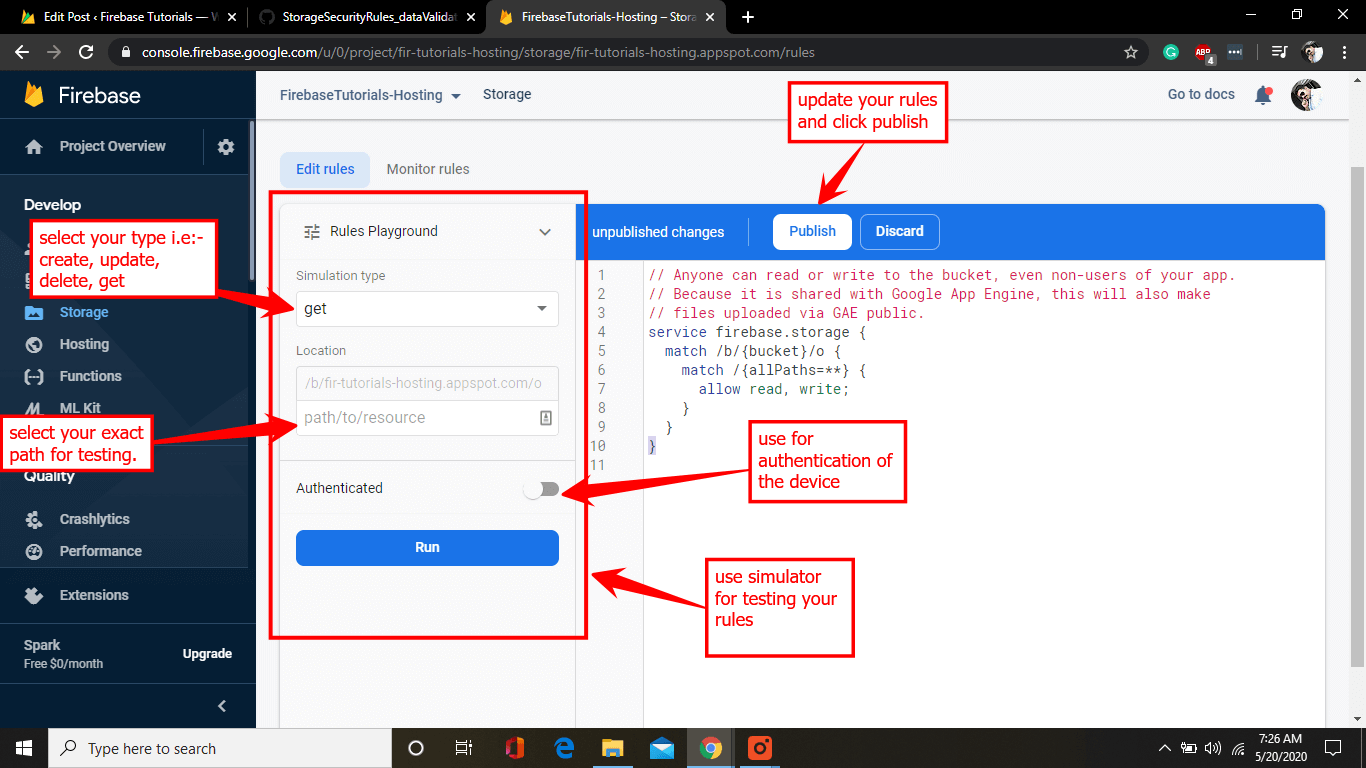
Herein you can update your security rules and make it published, but it’s always the best practice to test your rules in the simulator.
For a better understanding, you can watch the video embedded at the end of this tutorial that will help you to learn how the simulator works.
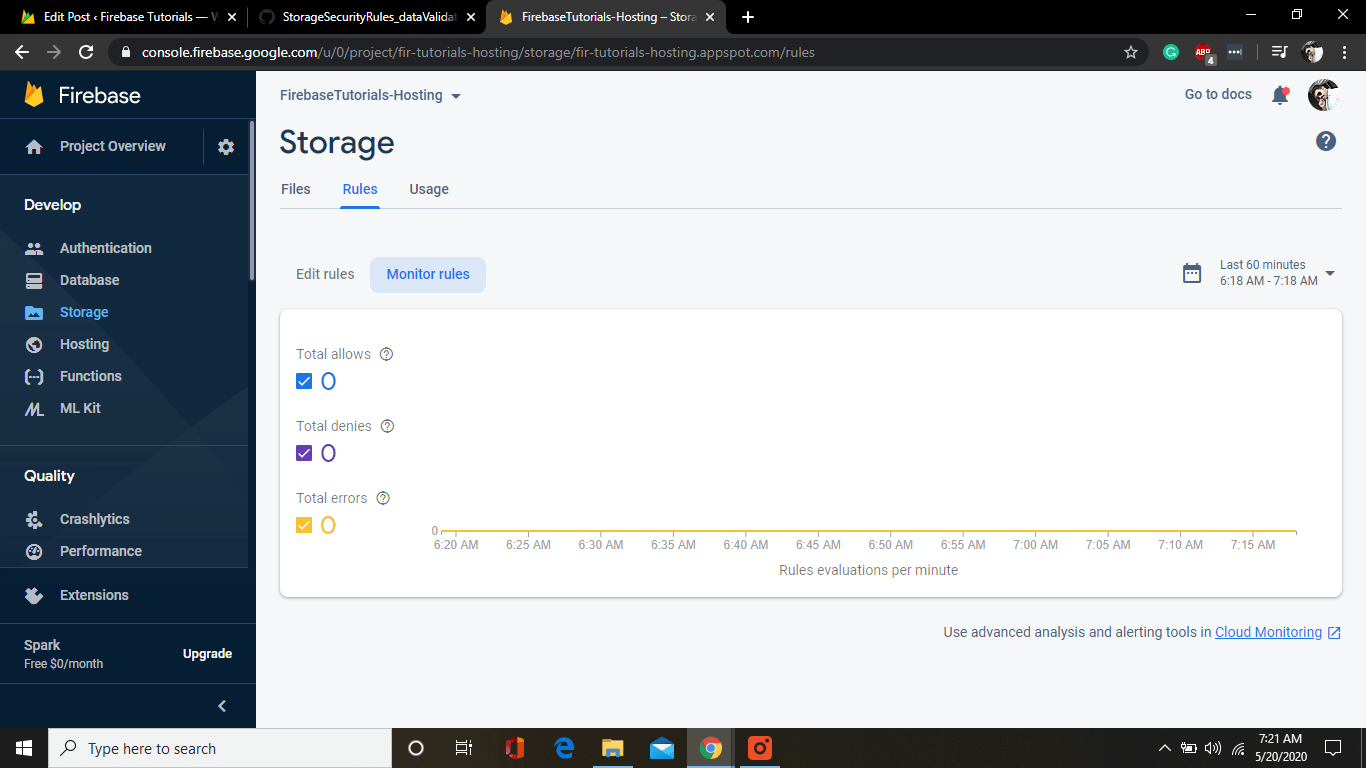
You can also monitor your rules and check your usage as well.
Learn How to Secure Files:
Storage Security Rules also helps you to secure your or your user files easily and quickly.
Understanding of Rules:
Firebase Storage Security Rules lets you assign the users who can or cannot access files that are stored on Cloud Storage.
Besides, how the files are managed and what kind of metadata they hold.
The basic rule is allow rule, which permits write and read requests if a condition is defined, Like
Matching Paths
Cloud Storage Rules match file paths that are used to obtain files in Storage. Security rules can match wildcard paths or exact same paths and Storage Security Rules can be nested. Suppose, If no matching rule allows a request method, or the required condition decides to false, then the request is rejected.
Exact Matches
- Here match is the keyword /images is the folder name, and profilephoto.png is the exact image that is stored on the Firebase Storage. You can place a rule directly in this way.
Nested Matches
You can also place rules in a nested way. For example, match/images {} will select all the images folder. Afterward, you can select the rest of the things.
Wildcard Matches
Security Rules can be applied to a pattern with the help of wildcards. The wildcard is just a named variable that describes either only string, i.e.,
profilePicture.png, or many path segments, Likeimages/profilePicture.png. You can create a wildcard by attaching curly(Middle) braces and add wildcard name inside it, for example{stringdemo}. You can also create a multiple segment wildcard just by adding=**to wildcard name, For example:{path=**}
Request Evaluation
Downloads, uploads, deletion, and metadata changes are decided using what is sent to Firebase storage. Each request (variable) that includes the path of the file where the request is actually being made, the exact time whenever the request is received. HTTP authentication and headers state are also appended.
Resource Evaluation
When deciding rules, maybe you want to judge the metadata of a particular file that is being downloaded, uploaded, deleted, or modified. This lets you build complex and robust rules that do stuff like only allow files with specific content types that need to be uploaded or only files that are greater than a particular size need to be deleted.
User-Based Security
Security Rules for Firebase cloud storage combine with Firebase auth service. In this way, the user gets a rich experience.
Authentication of the User:
Whenever a verified (authenticated) user operates a request on Firebase Storage, the request.auth (variable) pops up with the user’s Id (request.auth.uid) and it maintains the Firebase auth JWT (JSON Web Token) with the help of request.auth.token.
Public
A Security rule that does not admit
request.authcontext becomespublicrule because it does not recognize the auth context of a user. These security rules can help surface public data like gaming assets, sound, or some other static type content, etc.Private Authentication
In some cases, you want to show the data to all the users that are authenticated with your app and hide the data for unauthenticated users. Here the
request.auth(variable) is for every unauthenticated user.User Private
In most cases, a typical case of use for
request.auth. It will give singular users with appropriate permissions on their files: like uploading profile photos to reading the private documents.Private Group
One more fairly simple case of use will be to permit group permissions on a particular object, Like supporting many members of the team to help on a shared document. Here are a lot of ways in order to do that.
For better understanding, you can watch the video.
Ask any questions in the comment section below, our experts will be happy to help you at no extra cost.

1 thought on “Firebase Storage Rules (Visual Tutorial 2020)”
Comments are closed.